All day on the DARPA proposal effort
Category Archives: proposals
Phil 8.11.18
7:00 – ASRC BD
- Finishing up notes on the Evolution of Cooperation
- More proposal writing. Come at it from the creation of belief space maps, the benefits they provide in uncertain information (prediction, known topography, etc), what it takes to create them, and how they integrate with GIS
- 10:00 – 12:00 Will’s proposal
- haircut!
- 4:00 flu shot
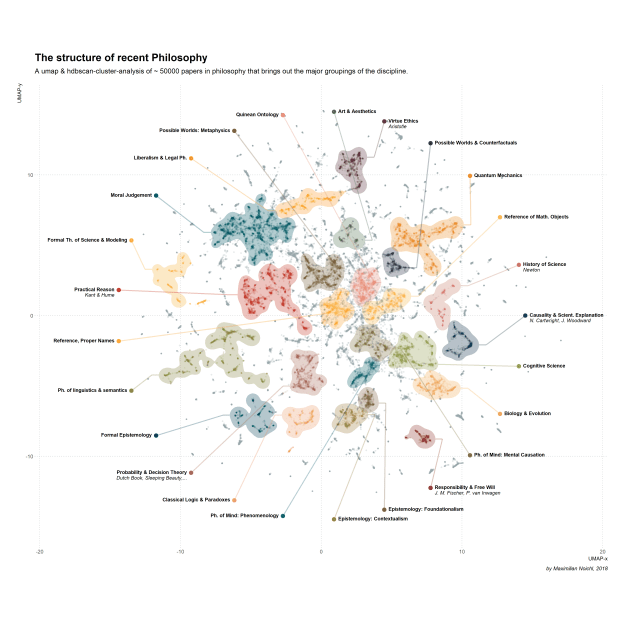 In this codebook we will investigate the macro-structure of philosophical literature. As a base for our investigation I have collected about fifty-thousand records from the Web of Science collection, spanning from the late forties to this very day.
In this codebook we will investigate the macro-structure of philosophical literature. As a base for our investigation I have collected about fifty-thousand records from the Web of Science collection, spanning from the late forties to this very day.
Phil 10.5.18
7:00 – 5:00 ASRC MKT
- Seasucker.com for roof racks?
- Continuing to write up notes from At Home in the Universe.
- Discussion with Matt about the deliverables for the Serial Interactions in Imperfect Information Games Applied to Complex Military Decision-Making (SI3-CMD) request
- DARPA proposal template
- Resized images for Aaron
- Biodiversity and the Balance of Nature
- As we destroy biological diversity, what else are we doing to the environment, what is being changed, and how will those changes affect us? One part of the answers to these questions is provided by Lawton and Brown’s consideration of redundancy (Chap. 12). Part of what the environment does for us involves “ecosystem services” — the movement of energy and nutrients through the air, water, and land, and through the food chains (Ehrlich, Foreword). Just how much biological diversity we need to keep the movement at approximately natural levels is a question of critical importance. Nonetheless, it is not a question that is commonly asked. A major synthesis of theories on the dynamics of nutrient cycling (DeAngelis 1991) devotes little space to the consequences of changes in the numbers of species per trophic level: It is the number of trophic levels that receives the attention. One might well conclude that, over broad limits, ecosystem services will continue to be provided, so long as there are some plants, some animals, some decomposers, and so on. Lawton and Brown conclude that numerous species are redundant.
Phil 10.4.18
7:00 – 5:30 ASRC MKT
- Join PCA! Write classified! Done
- There are 56 work days until Jan 1. My 400 hours is 50 days. So I go full time on research around the 22nd.
- Got a note from Wayne saying that there were 25 blue sky papers and 3 slots. THat might me expanded to 6 slots
- Write up notes on “At Home in the Universe” – started
- Finish speaking notes for BAA – Done
- Matt found a couple of things that might be good. One is due on October 16th, which is waaaaaaaaaaaaayyyyyyyy too tight.
- Looked at the Health.mil Connected Health clearinghouse effort and website. It sounds a lot like a military version of PubMed, with the ability to request reports on demand, plus some standardized reports as well. These reports seem to source back to other agencies like the CDC, with external SMEs.
Phil 8.12.18
7:00 – 4:00 ASRC MKT
- Having an interesting chat on recommenders with Robin Berjon on Twitter
- Long, but looks really good Neural Processes as distributions over functions
- Neural Processes (NPs) caught my attention as they essentially are a neural network (NN) based probabilistic model which can represent a distribution over stochastic processes. So NPs combine elements from two worlds:
- Deep Learning – neural networks are flexible non-linear functions which are straightforward to train
- Gaussian Processes – GPs offer a probabilistic framework for learning a distribution over a wide class of non-linear functions
Both have their advantages and drawbacks. In the limited data regime, GPs are preferable due to their probabilistic nature and ability to capture uncertainty. This differs from (non-Bayesian) neural networks which represent a single function rather than a distribution over functions. However the latter might be preferable in the presence of large amounts of data as training NNs is computationally much more scalable than inference for GPs. Neural Processes aim to combine the best of these two worlds.
- Neural Processes (NPs) caught my attention as they essentially are a neural network (NN) based probabilistic model which can represent a distribution over stochastic processes. So NPs combine elements from two worlds:
- How The Internet Talks (Well, the mostly young and mostly male users of Reddit, anyway)
- To get a sense of the language used on Reddit, we parsed every comment since late 2007 and built the tool above, which enables you to search for a word or phrase to see how its popularity has changed over time. We’ve updated the tool to include all comments through the end of July 2017.
- Add breadcrumbs to slides
- Download videos – done! Put these in the ppt backup
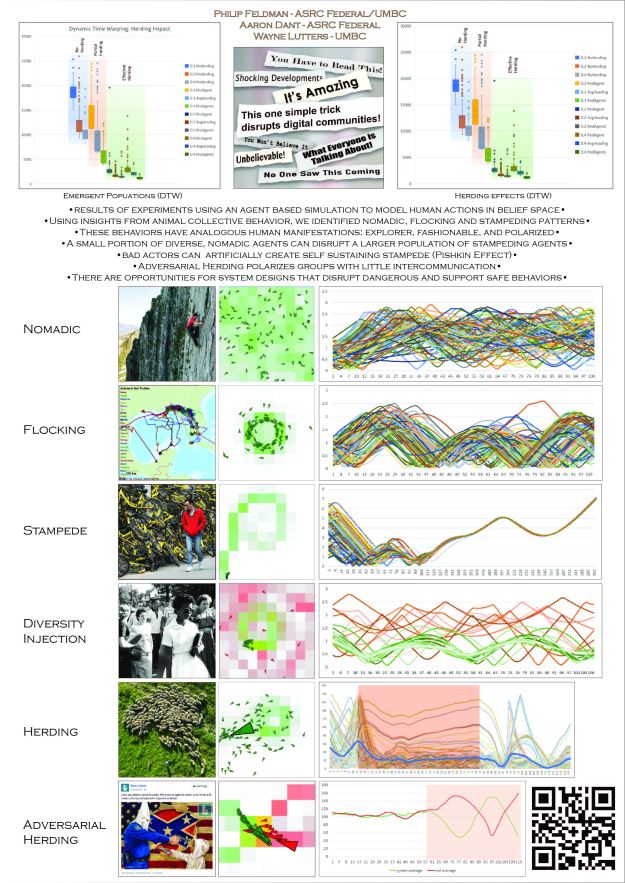
- Fix the DTW emergent population chart on the poster and in the slides. Print!
- Set up the LaTex Army BAA framework
- Slide walkthough. Good timing. Working on the poster some more
Phil 6.6.18
7:00 – 4:30 ASRC MKT
- Finished the white paper
- Peer review of Dr. Li’s AIMS work
- Computational Propaganda in the United States of America: Manufacturing Consensus Online
- Do bots have the capacity to influence the flow of political information over social media? This working paper answers this question through two methodological avenues: A) a qualitative analysis of how political bots were used to support United States presidential candidates and campaigns during the 2016 election, and B) a network analysis of bot influence on Twitter during the same event. Political bots are automated software programs that operate on social media, written to mimic real people in order to manipulate public opinion. The qualitative findings are based upon nine months of fieldwork on the campaign trail, including interviews with bot makers, digital campaign strategists, security consultants, campaign staff, and party officials. During the 2016 campaign, a bipartisan range of domestic and international political actors made use of political bots. The Republican Party, including both self-proclaimed members of the “alt-right” and mainstream members, made particular use of these digital political tools throughout the election. Meanwhile, public conversation from campaigners and government representatives is inconsistent about the political influence of bots. This working paper provides ethnographic evidence that bots affect information flows in two key ways: 1) by “manufacturing consensus,” or giving the illusion of significant online popularity in order to build real political support, and 2) by democratizing propaganda through enabling nearly anyone to amplify online interactions for partisan ends. We supplement these findings with a quantitative network analysis of the influence bots achieved within retweet networks of over 17 million tweets, collected during the 2016 US election. The results of this analysis confirm that bots reached positions of measurable influence during the 2016 US election. Ultimately, therefore, we find that bots did affect the flow of information during this particular event. This mixed methods approach shows that bots are not only emerging as a widely-accepted tool of computational propaganda used by campaigners and citizens, but also that bots can influence political processes of global significance.
Phil 6.5.18
7:00 – 6:00 ASRC
- Read the SASO comments. Most are pretty good. My reviewer #2 was #3 this time. There is some rework that’s needed. Most of the comments are good, even the angry ones from #3, which are mostly “where is particle swarm optimization???”
- Got an example quad chart from Helena that I’m going to base mine on
- Neat thing from Brian F:

- Lots. Of. White. Paper.
Phil 6.4.18
7:00 – 4:00 ASRC MKT
- Got accepted to SASO!
- Listening to a show about energy in bitcoin mining. There are ramifications to AI, since that’s also expensive processing.
- Thinking about the ramifications of ‘defect always’ emerging in a society.
- More Bit by Bit
- Quad chart
- Fika
Phil 6.1.18
7:00 – 6:00 ASRC MKT
- Bot stampede reaction to “evolution” in a thread about UNIX. This is in this case posting scentiment against the wrong thing. There are layers here though. It can also be advertising. Sort of the dark side of diversity injection.
- Seems like an explore/exploit morning
- Autism on “The Leap”: Neurotypical and Neurodivergent (Neurodiversity)
- From a BBC Business Daily show on Elon Musk
- Thomas Astebro (Decision Science): The return to independent invention: evidence of unrealistic optimism, risk seeking or skewness loving?
- Examining a sample of 1,091 inventions I investigate the magnitude and distribution of the pre‐tax internal rate of return (IRR) to inventive activity. The average IRR on a portfolio investment in these inventions is 11.4%. This is higher than the risk‐free rate but lower than the long‐run return on high‐risk securities and the long‐run return on early‐stage venture capital funds. The portfolio IRR is significantly higher, for some ex anteidentifiable classes of inventions. The distribution of return is skew: only between 7‐9% reach the market. Of the 75 inventions that did, six realised returns above 1400%, 60% obtained negative returns and the median was negative.
- Thomas Astebro (Decision Science): The return to independent invention: evidence of unrealistic optimism, risk seeking or skewness loving?
- Myth of first mover advantage
- Conventional wisdom would have us believe that it is always beneficial to be first – first in, first to market, first in class. The popular business literature is full of support for being first and legions of would-be business leaders, steeped in the Jack Welch school of business strategy, will argue this to be the case. The advantages accorded to those who are first to market defines the concept of First Mover Advantage (FMA). We outline why this is not the case, and in fact, that there are conditions of applicability in order for FMA to hold (and these conditions often do not hold). We also show that while there can be advantages to being first, from an economic perspective, the costs generally exceed the benefits, and the full economics of FMA are usually a losing proposition. Finally, we show that increasingly, we live in a world where FMA is eclipsed by innovation and format change, rendering the FMA concept obsolete (i.e. strategic obsolescence).
- More Bit by Bit
- Investigating the Effects of Google’s Search Engine Result Page in Evaluating the Credibility of Online News Sources
- Recent research has suggested that young users are not particularly skilled in assessing the credibility of online content. A follow up study comparing students to fact checkers noticed that students spend too much time on the page itself, while fact checkers performed “lateral reading”, searching other sources. We have taken this line of research one step further and designed a study in which participants were instructed to do lateral reading for credibility assessment by inspecting Google’s search engine result page (SERP) of unfamiliar news sources. In this paper, we summarize findings from interviews with 30 participants. A component of the SERP noticed regularly by the participants is the so-called Knowledge Panel, which provides contextual information about the news source being searched. While this is expected, there are other parts of the SERP that participants use to assess the credibility of the source, for example, the freshness of top stories, the panel of recent tweets, or a verified Twitter account. Given the importance attached to the presence of the Knowledge Panel, we discuss how variability in its content affected participants’ opinions. Additionally, we perform data collection of the SERP page for a large number of online news sources and compare them. Our results indicate that there are widespread inconsistencies in the coverage and quality of information included in Knowledge Panels.
- White paper
- Add something about geospatial mapping of belief.
- Note that belief maps are cultural artifacts, so comparing someone from one belief space to others in a shared physical belief environment can be roughly equivalent to taking the dot product of the belief space vectors that you need to compare. This could produce a global “alignment map” that can suggest how aligned, opposed, or indifferent a population might be with respect to an intervention, ranging from medical (Ebola teams) to military (special forces operations).
- Similar maps related to wealth in Rwanda based on phone metadata: Blumenstock, Joshua E., Gabriel Cadamuro, and Robert On. 2015. “Predicting Poverty and Wealth from Mobile Phone Metadata.” Science350 (6264):1073–6. https://doi.org/10.1126/science.aac4420.

- Similar maps related to wealth in Rwanda based on phone metadata: Blumenstock, Joshua E., Gabriel Cadamuro, and Robert On. 2015. “Predicting Poverty and Wealth from Mobile Phone Metadata.” Science350 (6264):1073–6. https://doi.org/10.1126/science.aac4420.
- Added a section about how mapping belief maps would afford prediction about local belief, since overall state, orientation and velocity could be found for some individuals who are geolocated to that area and then extrapolated over the region.
Phil 5.31.18
7:00 – ASRC MKT
- Via BBC Business Daily, found this interesting post on diversity injection through lunch table size:
- ‘People Analytics’ Through SuperCharged ID Badges (MIT Sloan)
- Humanyze helps companies make surprising connections about what makes employees effective.
- Data from the lunchroom could inform the boardroom
- Does lunch table size impact workplace productivity? By using analytics and mapping interactions, we found that increasing lunch table size boosted performance by 10%. And the approach has implications reaching far beyond the cafeteria.
- ‘People Analytics’ Through SuperCharged ID Badges (MIT Sloan)
- KQED is playing America Abroad – today on russian disinfo ops:
- Sowing Chaos: Russia’s Disinformation Wars
- Revelations of Russian meddling in the 2016 US presidential election were a shock to Americans. But it wasn’t quite as surprising to people in former Soviet states and the EU. For years they’ve been exposed to Russian disinformation and slanted state media; before that Soviet propaganda filtered into the mainstream. We don’t know how effective Russian information warfare was in swaying the US election. But we do know these tactics have roots going back decades and will most likely be used for years to come. This hour, we’ll hear stories of Russian disinformation and attempts to sow chaos in Europe and the United States. We’ll learn how Russia uses its state-run media to give a platform to conspiracy theorists and how it invites viewers to doubt the accuracy of other news outlets. And we’ll look at the evolution of internet trolling from individuals to large troll farms. And — finally — what can be done to counter all this?
- Sowing Chaos: Russia’s Disinformation Wars
- Some interesting papers on the “Naming Game“, a form of coordination where individuals have to agree on a name for something. This means that there is some kind of dimension reduction involved from all the naming possibilities to the agreed-on name.
- The Grounded Colour Naming Game
- Colour naming games are idealised communicative interactions within a population of artificial agents in which a speaker uses a single colour term to draw the attention of a hearer to a particular object in a shared context. Through a series of such games, a colour lexicon can be developed that is sufficiently shared to allow for successful communication, even when the agents start out without any predefined categories. In previous models of colour naming games, the shared context was typically artificially generated from a set of colour stimuli and both agents in the interaction perceive this environment in an identical way. In this paper, we investigate the dynamics of the colour naming game in a robotic setup in which humanoid robots perceive a set of colourful objects from their own perspective. We compare the resulting colour ontologies to those found in human languages and show how these ontologies reflect the environment in which they were developed.
- Group-size Regulation in Self-Organised Aggregation through the Naming Game
- In this paper, we study the interaction effect between the naming game and one of the simplest, yet most important collective behaviour studied in swarm robotics: self-organised aggregation. This collective behaviour can be seen as the building blocks for many others, as it is required in order to gather robots, unable to sense their global position, at a single location. Achieving this collective behaviour is particularly challenging, especially in environments without landmarks. Here, we augment a classical aggregation algorithm with a naming game model. Experiments reveal that this combination extends the capabilities of the naming game as well as of aggregation: It allows the emergence of more than one word, and allows aggregation to form a controllable number of groups. These results are very promising in the context of collective exploration, as it allows robots to divide the environment in different portions and at the same time give a name to each portion, which can be used for more advanced subsequent collective behaviours.
- The Grounded Colour Naming Game
- More Bit by Bit. Could use some worked examples. Also a login so I’m not nagged to buy a book I own.
- Descriptive and injunctive norms – The transsituational influence of social norms.
- Three studies examined the behavioral implications of a conceptual distinction between 2 types of social norms: descriptive norms, which specify what is typically done in a given setting, and injunctive norms, which specify what is typically approved in society. Using the social norm against littering, injunctive norm salience procedures were more robust in their behavioral impact across situations than were descriptive norm salience procedures. Focusing Ss on the injunctive norm suppressed littering regardless of whether the environment was clean or littered (Study 1) and regardless of whether the environment in which Ss could litter was the same as or different from that in which the norm was evoked (Studies 2 and 3). The impact of focusing Ss on the descriptive norm was much less general. Conceptual implications for a focus theory of normative conduct are discussed along with practical implications for increasing socially desirable behavior.
- Construct validity centers around the match between the data and the theoretical constructs. As discussed in chapter 2, constructs are abstract concepts that social scientists reason about. Unfortunately, these abstract concepts don’t always have clear definitions and measurements.
- Simulation is a way of implementing theoretical constructs that are measurable and testable.
- Descriptive and injunctive norms – The transsituational influence of social norms.
- Hyperparameter Optimization with Keras
- Recognizing images from parts Kaggle winner
- White paper
- Storyboard meeting
- The advanced analytics division(?) needs a modeling and simulation department that builds models that feed ML systems.
- Meeting with Steve Specht – adding geospatial to white paper
Phil 5.30.18
7:15 – 6:00 ASRC MKT
- More Bit by Bit
- An interesting tweet about the dichotomy between individual and herd behaviors.
- More white paper. Add something about awareness horizon, and how maps change that from a personal to a shared reality (cite understanding ignorance?)
- Great discussion with Aaron about incorporating adversarial herding. I think that there will be three areas
- Thunderdome – affords adversarial herding. Users have to state their intent before joining a discussion group. Bots and sock puppets allowed
- Clubhouse – affords discussion with chosen individuals. THis is what I thought JuryRoom was
- JuryRoom – fully randomized members and topics, based on activity in the Clubhouse and Thunderdome
Phil 5.29.18
Insane, catastrophic rain this weekend. That’s the top of a guardrail in the middle of the scene below:
7:00 – 4:30 ASRC MKT
- The Neural Representation of Social Networks
- The computational demands associated with navigating large, complexly bonded social groups are thought to have significantly shaped human brain evolution. Yet, research on social network representation and cognitive neuroscience have progressed largely independently. Thus, little is known about how the human brain encodes the structure of the social networks in which it is embedded. This review highlights recent work seeking to bridge this gap in understanding. While the majority of research linking social network analysis and neuroimaging has focused on relating neuroanatomy to social network size, researchers have begun to define the neural architecture that encodes social network structure, cognitive and behavioral consequences of encoding this information, and individual differences in how people represent the structure of their social world.
- This website is amazing, linear algebra with interactive examples. Vectors, matrix, dot product, etc, cool resource for learning http://immersivemath.com/ila/index.html
- Web Literacy for Student Fact-Checkers: …and other people who care about facts.
- Author: Mike Caulfield
- We Should Put Fact-Checking Tools In the Core Browser
- Years ago when the web was young, Netscape (Google it, noobs!) decided on its metaphor for the browser: it was a “navigator”. <—— this!!!!
- Navigator: a person who directs the route or course of a ship, aircraft, or other form of transportation, especially by using instruments and maps.
- Browser: a person who looks casually through books or magazines or at things for sale.
- Years ago when the web was young, Netscape (Google it, noobs!) decided on its metaphor for the browser: it was a “navigator”. <—— this!!!!
- Deep Learning Hunts for Signals Among the Noise
- Interesting article that indicates that deep learning generalizes through some form of compression. If that’s true, then the teurons and layers are learning how to coordinate (who recognizes what), which means dimension reduction and localized alignment (what are the features that make a person vs. a ship). Hmmm.
- Shwartz-Ziv, R., and Tishby, N.
Opening the Black Box of Deep Neural Networks via Information. ArXiv: https://arxiv.org/abs/1703.00810Zhang, C., Bengio, S., Hardt, M., Recht, B., and Vinyalis, O.
Understanding Deep Learning Requires Rethinking Generalization. ArXiV: https://arxiv.org/abs/1611.03530Poggio, T., Liao, Q., Miranda, B., Rosasco, L., Boix, X., Hidary, J., and Mhaskar, H.
Theory of Deep Learning III: Explaining the Non-Overfitting Puzzle. CBMM Memo 073 (2017). https://cbmm.mit.edu/sites/default/files/publications/CBMM-Memo-073.pdfAchille, A., Rovere, M., and Soatto, S.
Critical Learning Periods in Deep Neural Networks. UCLA-TR-170017. ArXiV: https://arxiv.org/abs/1711.08856
- Shwartz-Ziv, R., and Tishby, N.
- Interesting article that indicates that deep learning generalizes through some form of compression. If that’s true, then the teurons and layers are learning how to coordinate (who recognizes what), which means dimension reduction and localized alignment (what are the features that make a person vs. a ship). Hmmm.
- More Bit by Bit
- Really enjoying Casualties of Cool, btw. Lovely sound layering. Reminds me of Dark Side of the Moon / Wish you were here Pink Floyd
- Why you need to improve your training data, and how to do it
- No scrum today
- Travel briefing – charge to conference code
- Complexity Explorables
- Ride my Kuramotocycle!
- This explorable illustrates the Kuramoto model for phase coupled oscillators. This model is used to describe synchronization phenomena in natural systems, e.g. the flash synchronization of fire flies or wall-mounted clocks. The model is defined as a system of NN oscillators. Each oscillator has a phase variable θn(t)θn(t) (illustrated by the angular position on a circle below), and an angular frequency ωnωn that captures how fast the oscillator moves around the circle.
- Into the Dark
- This explorable illustrates how a school of fish can collectively find an optimal location, e.g. a dark, unexposed region in their environment simply by light-dependent speed control. The explorable is based on the model discussed in Flock’n Roll, which you may want to explore first. This is how it works: The swarm here consists of 100 individuals. Each individual moves around at a constant speed and changes direction according to three rules
- Ride my Kuramotocycle!
- More cool software: Kepler.gl is a powerful open source geospatial analysis tool for large-scale data sets.
- White paper. Good progress! I like the conclusions
Phil 5.25.18
7:00 – 4:30 ASRC MKT
- Reading more Bit by Bit. At the end of chapter two, Salganik mentions inference graphs, which made me think of Markov Chains which led me to Judea Pearl. Interesting morning.
- Sprint review
- More white paper writing
Phil 5.24.18
7:00 ASRC
- Is Bitcoin alive? Local organization and global entropy:

- Tweaked my terms page a bit
- Continuing Bit by Bit. Nicely written. currently reading about the pros and cons of using big data. It’s making me think about how to structure the Jury Room data so that it lends itself better to prolonged research.
- A gentle introduction to Doc2Vec
- In this post you will learn what is doc2vec, how it’s built, how it’s related to word2vec, what can you do with it, hopefully with no mathematic formulas.
- The combination of tags and paragraph/document ID could make this very nice for JuryRoom
- 1:30 CoE meeting
- 2:00 Meeting with Anton
Phil 5.25.18
7:00 – 6:00 ASRC MKT
- Starting Bit by Bit
- I realized the hook for the white paper is the military importance of maps. I found A Revolution in Military Cartography?: Europe 1650-1815
- Military cartography is studied in order to approach the role of information in war. This serves as an opportunity to reconsider the Military Revolution and in particular changes in the eighteenth century. Mapping is approached not only in tactical, operational and strategic terms, but also with reference to the mapping of war for public interest. Shifts in the latter reflect changes in the geography of European conflict.
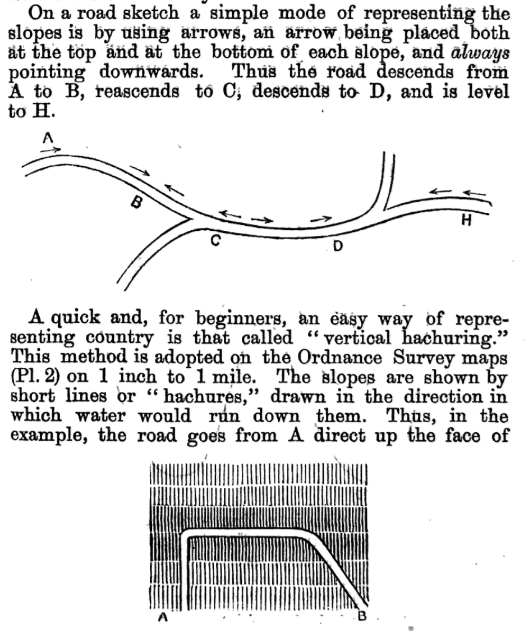
- Reconnoitering sketch from Instructions in the duties of cavalry reconnoitring an enemy; marches; outposts; and reconnaissance of a country; for the use of military cavalry. 1876 (pg 83)
- A rutter is a mariner’s handbook of written sailing directions. Before the advent of nautical charts, rutters were the primary store of geographic information for maritime navigation.
- It was known as a periplus (“sailing-around” book) in classical antiquity and a portolano (“port book”) to medieval Italian sailors in the Mediterranean Sea. Portuguese navigators of the 16th century called it a roteiro, the French a routier, from which the English word “rutter” is derived. In Dutch, it was called a leeskarte (“reading chart”), in German a Seebuch (“sea book”), and in Spanish a derroterro
- Example from ancient Greece:
- From the mouth of the Ister called Psilon to the second mouth is sixty stadia.
- Thence to the mouth called Calon forty stadia.
- From Calon to Naracum, which last is the name of the fourth mouth of the Ister, sixty stadia.
- Hence to the fifth mouth a hundred and twenty stadia.
- Hence to the city of Istria five hundred stadia.
- From Istria to the city of Tomea three hundred stadia.
- From Tomea to the city of Callantra, where there is a port, three hundred stadia
- Battlespace
- A term used to signify a unified military strategy to integrate and combine armed forces for the military theatre of operations, including air, information, land, sea, cyber and space to achieve military goals. It includes the environment, factors, and conditions that must be understood to successfully apply combat power, protect the force, or complete the mission. This includes enemy and friendly armed forces, infrastructure, weather, terrain, and the electromagnetic spectrum within the operational areas and areas of interest
- Cyber-Human Systems (CHS)
- In a world in which computers and networks are increasingly ubiquitous, computing, information, and computation play a central role in how humans work, learn, live, discover, and communicate. Technology is increasingly embedded throughout society, and is becoming commonplace in almost everything we do. The boundaries between humans and technology are shrinking to the point where socio-technical systems are becoming natural extensions to our human experience – second nature, helping us, caring for us, and enhancing us. As a result, computing technologies and human lives, organizations, and societies are co-evolving, transforming each other in the process. Cyber-Human Systems (CHS) research explores potentially transformative and disruptive ideas, novel theories, and technological innovations in computer and information science that accelerate both the creation and understanding of the complex and increasingly coupled relationships between humans and technology with the broad goal of advancing human capabilities: perceptual and cognitive, physical and virtual, social and societal.
- Reworked Section 1 to incorporate all this in a single paragraph
- Long discussion about all of the above with Aaron
- Worked on getting the CoE together by CoB
- Do Diffusion Protocols Govern Cascade Growth?
- Large cascades can develop in online social networks as people share information with one another. Though simple reshare cascades have been studied extensively, the full range of cascading behaviors on social media is much more diverse. Here we study how diffusion protocols, or the social exchanges that enable information transmission, affect cascade growth, analogous to the way communication protocols define how information is transmitted from one point to another. Studying 98 of the largest information cascades on Facebook, we find a wide range of diffusion protocols – from cascading reshares of images, which use a simple protocol of tapping a single button for propagation, to the ALS Ice Bucket Challenge, whose diffusion protocol involved individuals creating and posting a video, and then nominating specific others to do the same. We find recurring classes of diffusion protocols, and identify two key counterbalancing factors in the construction of these protocols, with implications for a cascade’s growth: the effort required to participate in the cascade, and the social cost of staying on the sidelines. Protocols requiring greater individual effort slow down a cascade’s propagation, while those imposing a greater social cost of not participating increase the cascade’s adoption likelihood. The predictability of transmission also varies with protocol. But regardless of mechanism, the cascades in our analysis all have a similar reproduction number (≈ 1.8), meaning that lower rates of exposure can be offset with higher per-exposure rates of adoption. Last, we show how a cascade’s structure can not only differentiate these protocols, but also be modeled through branching processes. Together, these findings provide a framework for understanding how a wide variety of information cascades can achieve substantial adoption across a network.
- Continuing with creating the Simplest LSTM ever


You must be logged in to post a comment.