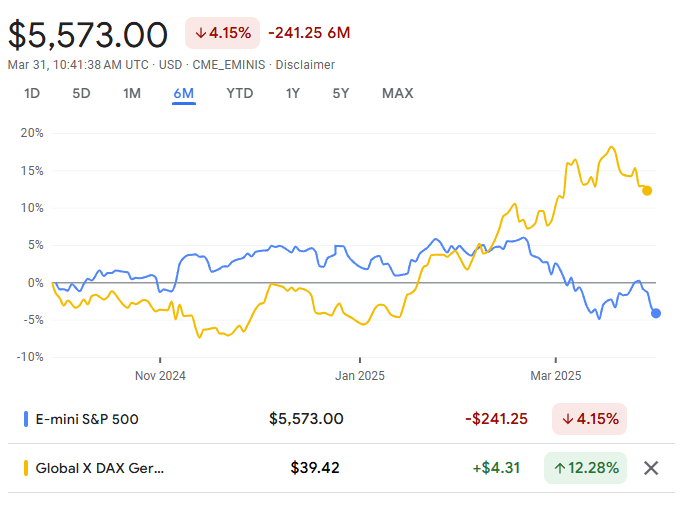
The effects of policy in one image (I’ve set the link to the page, to see current trends:
FAN: Fourier Analysis Networks
- Despite the remarkable successes of general-purpose neural networks, such as MLPs and Transformers, we find that they exhibit notable shortcomings in modeling and reasoning about periodic phenomena, achieving only marginal performance within the training domain and failing to generalize effectively to out-of-domain (OOD) scenarios. Periodicity is ubiquitous throughout nature and science. Therefore, neural networks should be equipped with the essential ability to model and handle periodicity. In this work, we propose FAN, a novel general-purpose neural network that offers broad applicability similar to MLP while effectively addressing periodicity modeling challenges. Periodicity is naturally integrated into FAN’s structure and computational processes by introducing the Fourier Principle. Unlike existing Fourier-based networks, which possess particular periodicity modeling abilities but are typically designed for specific tasks, our approach maintains the general-purpose modeling capability. Therefore, FAN can seamlessly replace MLP in various model architectures with fewer parameters and FLOPs. Through extensive experiments, we demonstrate the superiority of FAN in periodicity modeling tasks and the effectiveness and generalizability of FAN across a range of real-world tasks, e.g., symbolic formula representation, time series forecasting, language modeling, and image recognition.

SBIRs
- Looks like I’m stunt Aaron on and off for a while. Not sure if he will be in today
- 9:00 Sprint review – done
- 1:00 Art of the possible – done. Making a slide
- 3:00 Sprint planning – done
GPT Agents
- KA book
- Illusory Social Consensus: When silence is taken as agreement, how can we disrupt illusory consensus beliefs?








You must be logged in to post a comment.